
A death blow for PPTP
CloudCracker self-experimentation
by Jürgen Schmidt
Moxie Marlinspike's CloudCracker promises it can crack any PPTP connection – within a day, for $200. We tried it out with a real session.
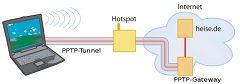
![]() The VPN creates an encoded tunnel that doesn't even give snoopers at a Wi-Fi hotspot a chance - or does it...
Companies primarily use virtual private networks (VPNs) to give employees working elsewhere secure access to the corporate network over the internet. VPNs are also often used to secure mobile devices' and smartphones' network connections when using, say, public hotspots, thereby locking out any curious snoopers. Whether it's a Windows, Mac OS X, or Linux machine, or a smartphone or a tablet, they all support Microsoft's Point-to-Point Tunneling Protocol (PPTP) out of the box, and, since it's so easy to set up, it's very popular.
The VPN creates an encoded tunnel that doesn't even give snoopers at a Wi-Fi hotspot a chance - or does it...
Companies primarily use virtual private networks (VPNs) to give employees working elsewhere secure access to the corporate network over the internet. VPNs are also often used to secure mobile devices' and smartphones' network connections when using, say, public hotspots, thereby locking out any curious snoopers. Whether it's a Windows, Mac OS X, or Linux machine, or a smartphone or a tablet, they all support Microsoft's Point-to-Point Tunneling Protocol (PPTP) out of the box, and, since it's so easy to set up, it's very popular.
The fact that it's actually not all that great at security is fairly well known. Still, many were surprised when, in late July, security researcher Moxie Marlinspike presented an online service that could crack the secret for authentication and encoding within a day. The theory looks plausible – and is very worrying. MSCHAPv2, the authentication protocol used for PPTP, uses outdated DES operations and can apparently be cracked easily using specialised hardware. More specifically, CloudCracker is said to be able to figure out the NT hash in logged network packets that serves as the foundation for the authentication and encoding of PPTP – and of WLANs with WPA2 and EAP/MS-CHAPv2.

![]() MS-CHAPv2 uses the NT hash to create three DES keys, which it uses to encode the server's challenge three times and then produce a response. The green areas are sent as plaintext
MS-CHAPv2 uses the NT hash to create three DES keys, which it uses to encode the server's challenge three times and then produce a response. The green areas are sent as plaintext
Since the attacker can eavesdrop on the challenge and response, CloudCracker therefore only needs to try out all 256 possible DES keys in order to find the right ones and put them together again into an NT hash. There's not much more standing in the way of breaking into a corporate network through a VPN backdoor. But so far the theory was just a theory. We wanted to really run through everything – and quickly bumped into some unexpected problems.
In order to not make it too easy for the cracker, we established a test connection to a PPTP server with a very good password. Produced by a generator, the 16-character Nao;hi2chie)toh1 was complicated enough to satisfy even strict password requirements. Then, we recorded an iPhone's PPTP login process on an encrypted WLAN by using the arpspoof tool. With the tool, all of the iPhone's network traffic was redirected using a Linux computer connected to the same network; the packets were saved in a PCAP file with tcpdump. In principle, that could happen to anyone using a Wi-Fi hotspot without them noticing.
A quick look confirmed that the entire login process really had been recorded:
$ tcpdump -n -r my-pptp-chap.cap
....
IP 193.99.XX.XX > 192.168.69.169: GREv1, call 45515, seq 5, ack 4, length 60:
CHAP, Challenge (0x01), id 111,Value e5df... , Name pptpXY.heise.de
IP 192.168.69.169 > 193.99.XX.XX: GREv1, call 39936, seq 6, ack 6, length 80:
CHAP, Response (0x02), id 111, Value d4528..., Name jutest
IP 193.99.XX.XX > 192.168.69.169: GREv1, call 45515, seq 7, ack 6, length 83:
CHAP, Success (0x03), id 111, Msg S=6E9...406 M=Access granted
The open source tool chapcrack was then supposed to extract the three DES-encoded hashes from this PCAP file and use them to make a token for CloudCracker, but at first the Python script didn't want to do its job. Even the included demo file only returned errors. A bug report and a few emails later, there was a solution for the compatibility problems with the version of Python used in Ubuntu 10.04 LTS – but still no hashes, since the program was closing without any readout. After a few more bug reports, Moxie localised the "dpkt" bug and sent another patch, which finally managed to activate chapcrack. In just a few seconds, the script spat out the extracted data:
$ ./chapcrack.py parse -i ./my-pptp-chap.cap
Got completed handshake [192.168.69.169 --> 193.99.XXX.YYY]
Cracking K3..............
User = jutest
C1 = 4de9d262a222e617
C2 = d5e0d1eb316886a6
C3 = 9a441fe1dc7001fe
P = 36b29bb9b0140fc0
K3 = d9c50000000000
CloudCracker Submission = $99$NrKbubAUD8BN6dJioiLmF9Xg0esxaIam2cU=
![]() Cracking MS-CHAPv2 is just one of CloudCracker's talents
Cracking MS-CHAPv2 is just one of CloudCracker's talents
The K3 key filled with zeroes was cracked immediately. The Python script used the challenge hashes to create the submission token that we then fed to CloudCracker to get the rest of the NT hash.
We paid the $200 for testing the 144,115,188,075,855,872 (2^56 * 2) keys with a credit card using a third-party payment service provider, and everything went smoothly – although there didn't seem to be any kind of receipt, and our emails asking about one went unacknowledged. After we entered our credit card details, the cloud service simply promised to send an email at some point.








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








