Security-through-isolation: Qubes 1.0 released
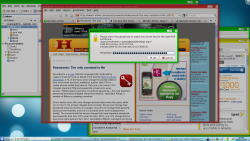
![]() The window colours show which VM domain the application belongs to; here a background application asks for a passphrase.
The window colours show which VM domain the application belongs to; here a background application asks for a passphrase.
Invisible Things Labs has completed development on Qubes after three years of work on the application-isolation-by-virtualisation Linux- and Xen-based operating system and released version 1.0. Joanna Rutkowska, CEO of Invisible Things Lab, said that creating the OS was a "a great challenge, especially for such a small team as ours, but ultimately, I'm very glad with the final outcome – it really is a stable and reasonably secure desktop OS".
The Qubes OS, first announced in April 2010, is designed to allow users to partition their work into lightweight Xen VMs, AppVMs, to isolate different groups of applications from each other and therefore reduce the damage that any one compromised application can do. The GUI on Qubes then brings the applications together so they all seem to run locally. Qubes is built on top of the Xen bare metal hypervisor; it places networking code in an unprivileged VM with none on a privileged domain.
It does rely on the user to at least partition their life in such a way as to reduce the dangers. Rutkowska points out that there are no formally proven secure general purpose operating systems and that Qubes approaches the security issue with a practical eye by minimising the number of sensitive parts in the OS and then focussing on securing the ones that remain.
Security decisions though, such as which permissions each domain should have or whether a particular document should be opened in the current domain or within it's own lightweight disposable VM, are decisions that the user has to take. This complexity of decisions has ramifications, says Rutkowska, in that Qubes requires an advanced user to make best use of the security options available to them. Users should be aware that just using Qubes will not automatically make them more secure.
"It's how they are going to use it might make them significantly more secure", says Rutkowska, explaining that an attack against Firefox will work in just the same way as it would on normal Linux, but under Qubes, if the attack occurred on Firefox running in a "personal use" domain and not in the "home banking" domain, then the damage has, at least, been contained.
The 1.0 release has seen the introduction of an improved Qubes Manager which includes a GUI for configuring "almost every aspect of the Qubes system". Its virtual machines are based on a Fedora 17 template. The developers have also added features such as a one click "Disposable Web Browser" and support for full screen mode for selected VMs. Installation and download links are available from the Qubes wiki. Source code is also available.
The Qubes developers found three serious security issues when developing the OS, including one in their own code, but are looking forward to seeing how people attack the Qubes security infrastructure.
Qubes 1.0 is also available from The H Downloads.
(djwm)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















